…AND THE PROBLEM WITH RELYING ON MICROSOFT ALONE It’s an interesting problem that we are seeing time and time again. Companies (and I’m not talking small ones either) relying on Microsoft to be their IP Address Management tool or to … Read More
Security
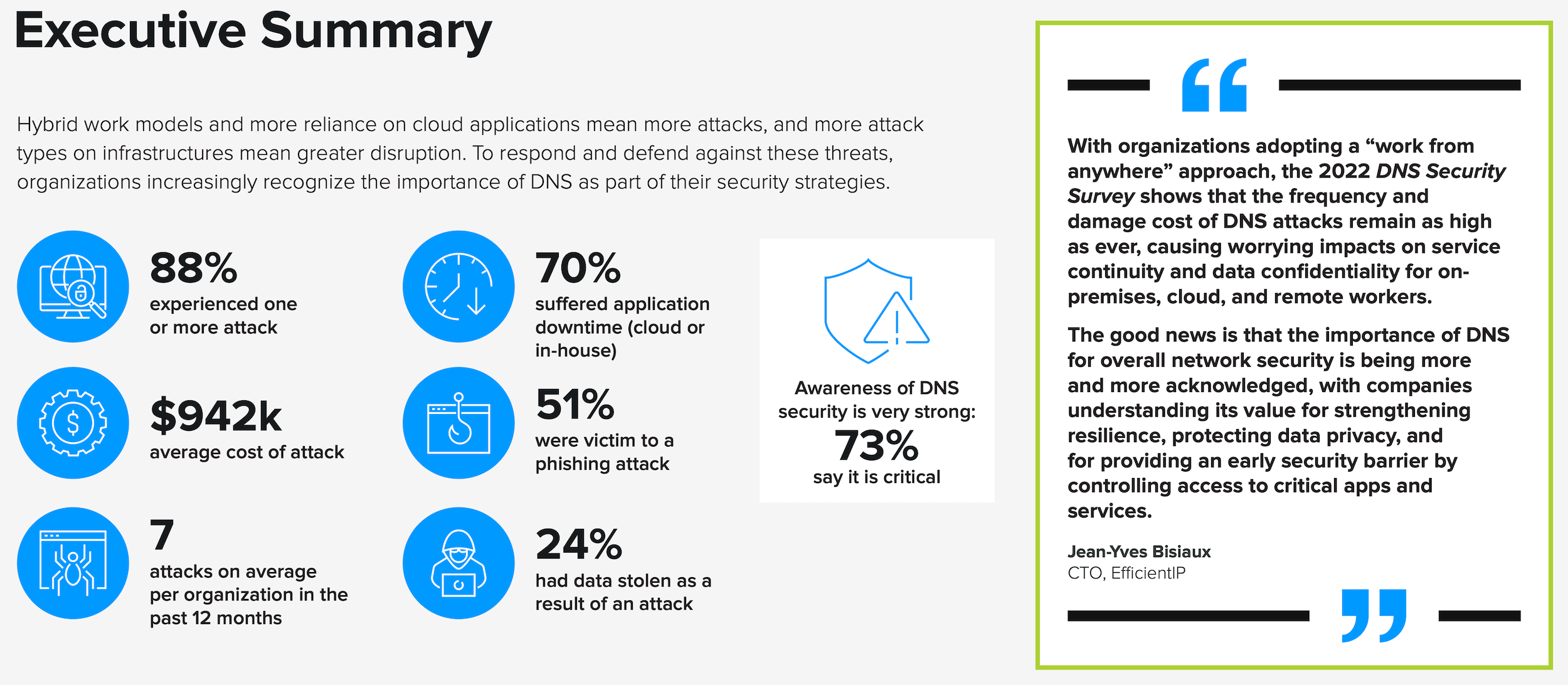
IDC 2022 Global DNS Threat Report
Securing Anywhere Networking DNS Security for Business Continuity and Resilience DNS has been the Achilles’ heel of the network since its creation, making it a target of choice for cybercriminals. These attacks exploit weaknesses, gain access to the network, and … Read More

DEVICE42 AND LOG4J ZERO-DAY
HOW DEVICE42 CAN HELP Device42’s discovery capability can help you identify systems vulnerable to the Log4j RCE the Log4j vulnerability is critical and impacts many applications and systems Device42’s software is not impacted by the Log4j vulnerability SUMMARY CertNZ revealed on … Read More
How can you troubleshoot your network issues and improve its security with a limited budget and a laptop?
Network issues and security problems can happen at any point, particularly when you are not prepared to respond appropriately and fast. To investigate these issues, you’ll need access to your network for 100% visibility of what is causing the problem. … Read More
CyberSeige with Spirent CyberFlood
This demo of the CyberFlood GUI creating attack traffic and emulating any country in the world is a powerful solution to not only tune perimeter devices but to also help train cyber teams to understand types of attack traffic. When … Read More
Transport Layer Security v1.3 Fuzz Testing
Improving security and robustness of Cloud, IoT, and Internet Services For over two decades, Secure Sockets Layer (SSL) and its successor Transport Layer Security (TLS) have been responsible for securing the communication in the network and between smart devices. The … Read More
Why would Europe’s General Data Protection Regulation (GDPR) Affect My Business?
In May 2018, the European Union’s (EU) General Data Protection Regulation (GDPR) will come into effect. It’s the most comprehensive piece of privacy legislation developed by any jurisdiction to date and goes way beyond the requirements of Australia’s current privacy … Read More
Why You Need to Test How Secure Your IoT Devices Are
By 2020 the number of Internet of Things (IoT) devices installed across the world will be more than twice the figure for 2017, according to analyst firm Gartner. There are already around 8.4 billion connected devices today and Gartner says … Read More
30 Days until Mandatory Data Breach Notification Becomes Law
Australia has recently enacted new legislation on the federal level to bring its data security practices in line with nations like the United States. This was initiated with the intent of streamlining international cooperation concerning data storage on a corporate … Read More
What’s the point of penetration testing?
With Australia’s recent introduction of a mandatory data breach notification regime, it’s more important than ever to invest in cyber security. If an organisation has grounds to believe that there has been an eligible data breach, it must notify customers … Read More

