Shield Against Invisible Cyber Threats
BreacHunt was born from a clear ambition: to provide a proactive and offensive approach to counter modern cyber threats. After conducting in-depth audits on technical, informational, and reputational threats, BreacHunt identified infostealers as one of the most impactful dangers for businesses and their sensitive data.
Strategic Detection and Information Analysis
That realisation marked a turning point in their journey: BreacHunt chose to focus their efforts on detecting, analysing, and neutralising infostealers. Since then, they have been developing innovative solutions to protect clients and prevent cyberattacks before they cause harm.
Helps
- Secure Critical Data
- Prevents Informational Threats
- Provide Real-Time Alerts

InfoStealers
Infostealers are malicious software designed to steal sensitive data. By analyzing and cross-referencing large volumes of exposed data, attackers can identify exploitable weaknesses. This intelligence enables them to launch targeted attacks, such as personalized phishing campaigns, deploying additional malware, or infiltrating corporate networks.
By combining data theft with a methodical exploitation of information, infostealers pose a particularly sophisticated threat, capable of orchestrating complex and difficult-to-counter attacks.
The process of a cyber attack from infection to exfiltration
- Infection:
The user is infected by an attack vector such as phishing, downloading an infected file, or exploiting a vulnerability. - Data Collection:
The malware steals sensitive information such as credentials, passwords, banking data, and browsing cookies. - Data Exfiltration:
The stolen data is sent to command and control (C2) servers, the dark web, or via encrypted emails. - Malicious Use:
Attackers exploit this data for fraud, identity theft, or resale on the Dark Web.
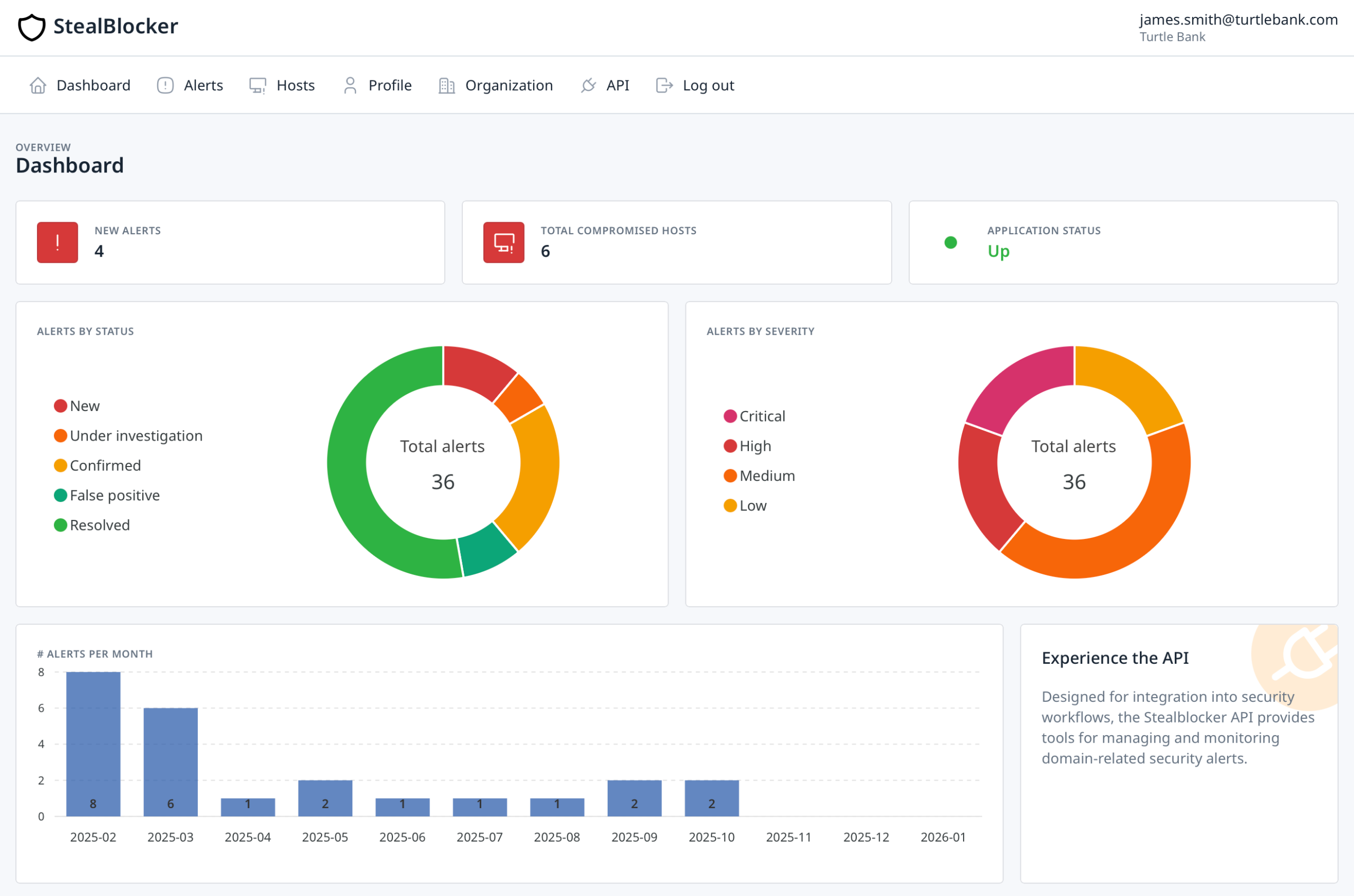

Stealblocker
Protect Your Data Against InfoStealers
Stealblocker alerts you whenever your credentials, targeted by infostealers, appear on the Dark Web. With precise analyses based on your domain names, it helps you anticipate and block the exploitation of compromised access.
- InfoStealer Detection:
Continuous monitoring of your sensitive data with alerts based on your domain names to identify and neutralize threats. - Attack Prevention:
A proactive approach to prevent the exploitation of compromised access credentials linked to your employees, suppliers, or customers. - Integration:
STEALBLOCKER also offers an API for advanced automation and enhanced responsiveness.
Stealreact
A Fast Response to InfoStealer Threats
With Stealreact, manage specific alerts targeting infostealers through a flexible token-based system. This innovative solution allows you to adopt a tailored strategy for each type of threat and ensure optimal protection of your critical data.
- Maximum Responsiveness:
Specific alerts are processed within 24 to 48 hours—ideal for recent or critical incidents. - Usage Flexibility:
Manage alerts by client or domain, based on your security priorities. - Flexible Management:
You receive a defined annual volume of tokens to use freely based on your alert needs. - Adaptability:
If you exceed your annual token volume, the first additional occurrence does not incur any charges, providing you with extra flexibility.
StealCheck
A Free and Personalised Diagnosis
With Stealreact, manage specific alerts targeting infostealers through a flexible token-based system. This innovative solution allows you to adopt a tailored strategy for each type of threat and ensure optimal protection of your critical data. See the link to StealCheck above or visit https://breachunt.com/stealcheck/.
In less than 48 hours, our analysts scan data breaches from the last three months to identify all compromises related to your professional domain.
You then receive a confidential and detailed report, including:
- The exact number of compromised credentials detected
- Their criticality level (Low, Medium, High, Critical)
- Concrete recommendations to reduce your exposure
- Optionally, a BreacHunt expert can present the results during a 30-minute exchange
The Results
Early detection of compromised credentials before exploitation
Identify stolen usernames, passwords, session tokens, and identity data exposed by infostealer malware or attacker ecosystems before they are used for lateral movement, ransomware, or data breaches.
Reduced breach impact and dwell time
Gain real-time intelligence and prioritised alerts that allow security teams to act quickly, contain risk, and significantly reduce the time attackers remain undetected in the environment.
Improved identity and access security posture
Strengthen IAM, Zero Trust, and SOC workflows by integrating breach intelligence into existing security controls, enabling faster credential resets, access revocation, and policy enforcement.
Proactive, intelligence-driven security operations
Move beyond reactive alerts to a forward-looking security model that continuously adapts to evolving attacker techniques, helping organisations stay ahead of modern threats rather than responding after damage is done.

BreacHunt is a French Threat Hunting-as-a-Service (THaaS) platform, specialized in proactive detection of weak signals. StealBlocker and StealReact services form a continuum of protection against threats from the dark web and compromised credentials.










